From Manual HR to Smart Automation: How Core HR & Payroll Software Drives Business Growth
In today’s fast-moving and competitive business environment, manual HR operations are no longer sustainable. Spreadsheets, paper files, and repetitive data entry slow down decision-making, increase human error, and drain valuable resources....

Smart Accounting & Financial Integration Software | KoriyalPlus
Streamlined Ledgers, Automated Entries & Daily Cash Flow InsightsIn today’s fast-moving microfinance and digital finance landscape, accurate and timely financial management is no longer optional—it is essential. Traditional accounting m...

Why Every Business Needs Core HR & Payroll Management Software in 2026
In 2026, rapid digital transformation through automation, AI, and cloud systems makes manual HR management outdated. Core HR & Payroll Management Software streamlines employee data, attendance, payroll, and compliance, helping organizat...
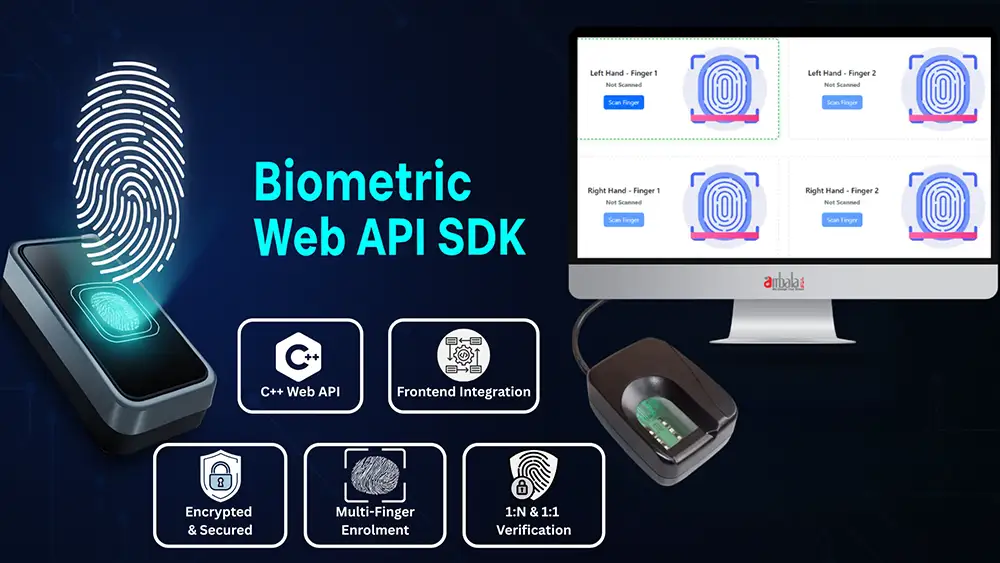
Biometric Web API SDK: The Easiest Way to Integrate Fingerprint Scanners into Web Applications
As biometric authentication becomes essential for modern security systems, developers need reliable and flexible tools to integrate fingerprint scanning into their web applications. The Biometric Web API SDK offers a complete end-to-end sol...

Smart Accounting & Financial Integration System: Streamlined Ledgers, Auto Entries & Real-Time Insights
In today’s dynamic world of microfinance and digital finance, managing financial data efficiently is critical to ensuring transparency and informed decision-making. Traditional systems relying on manual entries, spreadsheets, and paper-base...
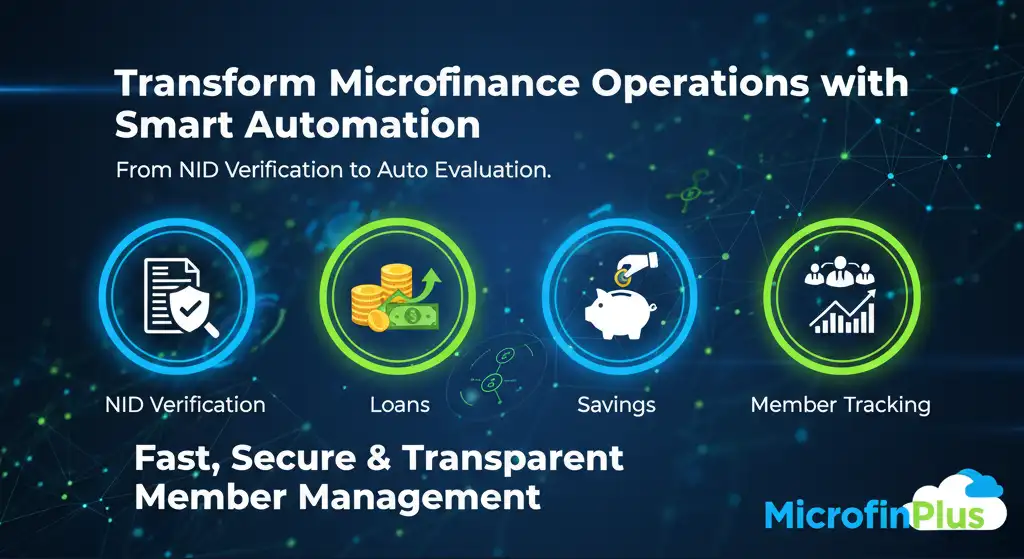
Transforming Microfinance Operations with a Smart Member Management System: From NID Verification to Auto Evaluation
The microfinance sector plays a pivotal role in empowering small entrepreneurs, farmers, and low-income communities. Yet, traditional operations often rely on manual data entry, paper-based records, and slow verification processes. These ch...

Building BlackOrigin: A Scalable Trading Bot for SaaS Marketplaces
We built BlackOrigin, a SaaS trading automation platform designed to execute lightning-fast trades on Bybit, powered by real-time TradingView signals.The mission was simple yet demanding: “Execute buy and sell orders instantly, size positi...

ShikkhaPlus: The All-in-One Educational Institution Management Software
In today’s fast-changing digital world, running an educational institution is no easy task. From managing student admissions to handling daily attendance, fee collections, examinations, and communication — every activity demands time, preci...

Cooperative Management Software | Automate Savings, Loans & Accounting with Cooperativebd Plus
In today’s fast-paced financial landscape, efficiency and transparency are the cornerstones of success. For cooperative societies, manual record-keeping and paper-based reporting often lead to inefficiency, errors, and delays. That’s where...

KoriyalPlus – Smart Accounting Management Software
KoriyalPlus – the Smart Accounting Management Software – comes in. It’s a modern, cloud-powered solution designed to simplify complex financial operations, reduce manual errors, and enhance decision-making through automation and analytics.W...